5月18日更新
很多网友表示Telnet无法解锁,若你使用本教程成功解锁或遇到问题劳烦你在下面评论区留言,感谢!
背景
当初为了刷OpenWRT购入WNR2000,然而当时只有v1 – v3支持第三方固件,在JD上买的却是v4啊,收到货瞬间(目瞪口呆.jpg)。吃灰几个月拿出来用,突发奇想查一波OpenWRT WIKI,果真已经支持了WNR2000v4。然而网上并没有详细教程啊..即立此坑
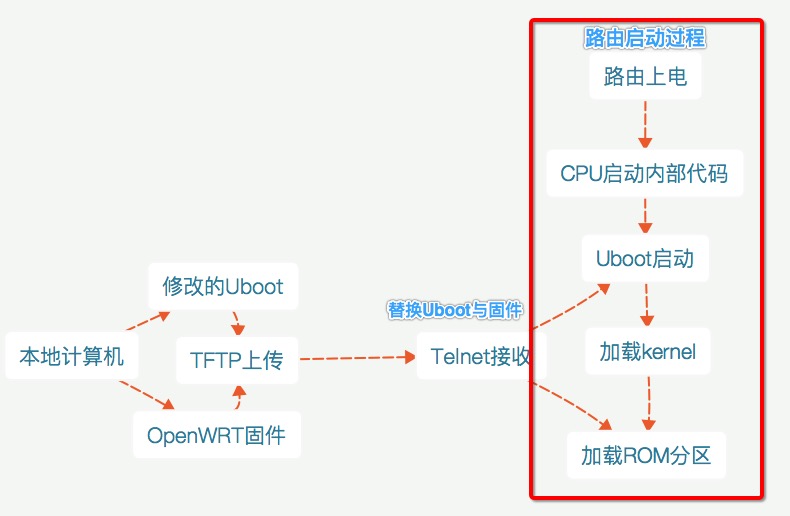
原理
大概流程:
1.通过Telnet访问路由
2.本地计算机搭建TFTP服务器
3.从下载存在TFTP的Uboot和固件
4.替换Unlock的Uboot以及OpenWRT
关于Uboot:Uboot是德国DENX小组开发、用于嵌入式CPU的Bootloader,它支持10多种不同的操作系统(包括x86架构)。其小巧速度快,已经成为了Atheros(高通)和Ralink(联发科)产品的标配引导系统,并且在所有嵌入式的引导系统中市场占有率最大。
所需准备
1.更新路由固件到1.0.0.58
WNR2000v4-Stock-Firmware version 1.0.0.58
2.下载修改好的uboot
uboot_env_bootcmd_nocrc.backup
3.下载 openwrt for wnr2000v4 并 将其更名为sysupgrade.bin
openwrt-15.05-ar71xx-generic-wnr2000v4-squashfs-sysupgrade.bin
4.[重要]使用网线连接路由器并将你的计算机ip设置为’192.168.1.10′
使用python发送UDP
需要使用telnet对路由执行刷机指令,所以刷机的门槛就在能否用telnet连接路由。Netgear的路由默认是打开了telnet:23端口的,可是无法直接访问,需要解锁。不同路由的解锁方法不同,这里我们使用Github提供的 telnetenable.py 发送UDP解锁。
https://github.com/insanid/netgear-telenetenable
此处需要使用 pycrypto 库
pip install pycryptotelnetenable.py
# Copyright (c) 2009 Paul Gebheim
#
# Permission is hereby granted, free of charge, to any person obtaining a copy
# of this software and associated documentation files (the "Software"), to deal
# in the Software without restriction, including without limitation the rights
# to use, copy, modify, merge, publish, distribute, sublicense, and/or sell
# copies of the Software, and to permit persons to whom the Software is
# furnished to do so, subject to the following conditions:
#
# The above copyright notice and this permission notice shall be included in
# all copies or substantial portions of the Software.
#
# THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
# IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
# FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
# AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
# LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM,
# OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN
# THE SOFTWARE.
import sys
import socket
import array
from optparse import OptionParser
from Crypto.Cipher import Blowfish
from Crypto.Hash import MD5
TELNET_PORT = 23
# The version of Blowfish supplied for the telenetenable.c implementation
# assumes Big-Endian data, but the code does nothing to convert the
# little-endian stuff it's getting on intel to Big-Endian
#
# So, since Crypto.Cipher.Blowfish seems to assume native endianness, we need
# to byteswap our buffer before and after encrypting it
#
# This helper does the byteswapping on the string buffer
def ByteSwap(data):
a = array.array('i')
if(a.itemsize < 4):
a = array.array('L')
if(a.itemsize != 4):
print "Need a type that is 4 bytes on your platform so we can fix the data!"
exit(1)
a.fromstring(data)
a.byteswap()
return a.tostring()
def GeneratePayload(mac, username, password=""):
# eventually reformat mac
mac = mac.replace(":","").upper()
# Pad the input correctly
assert(len(mac) < 0x10)
just_mac = mac.ljust(0x10, "\x00")
assert(len(username) <= 0x10)
just_username = username.ljust(0x10, "\x00")
assert(len(password) <= 0x21)
just_password = password.ljust(0x21, "\x00")
cleartext = (just_mac + just_username + just_password).ljust(0x70, '\x00')
md5_key = MD5.new(cleartext).digest()
payload = ByteSwap((md5_key + cleartext).ljust(0x80, "\x00"))
secret_key = "AMBIT_TELNET_ENABLE+" + password
return ByteSwap(Blowfish.new(secret_key, 1).encrypt(payload))
def SendPayload(ip, payload):
for res in socket.getaddrinfo(ip, TELNET_PORT, socket.AF_INET, socket.SOCK_DGRAM, socket.IPPROTO_IP):
af, socktype, proto, canonname, sa = res
try:
s = socket.socket(af, socktype, proto)
except socket.error, msg:
s = None
continue
try:
s.connect(sa)
except socket.error, msg:
s.close()
s= None
continue
break
if s is None:
print "Could not connect to '%s:%d'" % (ip, TELNET_PORT)
else:
s.send(payload)
s.close()
print "Sent telnet enable payload to '%s:%d'" % (ip, TELNET_PORT)
def main():
args = sys.argv[1:]
if len(args) < 3 or len(args) > 4:
print "usage: python telnetenable.py <ip> <mac> <username> [<password>]"
ip = args[0]
mac = args[1]
username = args[2]
password = ""
if len(args) == 4:
password = args[3]
payload = GeneratePayload(mac, username, password)
SendPayload(ip, payload)
main()执行 telnetenable.py 路由ip 路由MAC地址(大写并去除 “:” ) 路由用户 密码
Example:
python telnetenable.py 192.168.1.1 00405E21144E admin password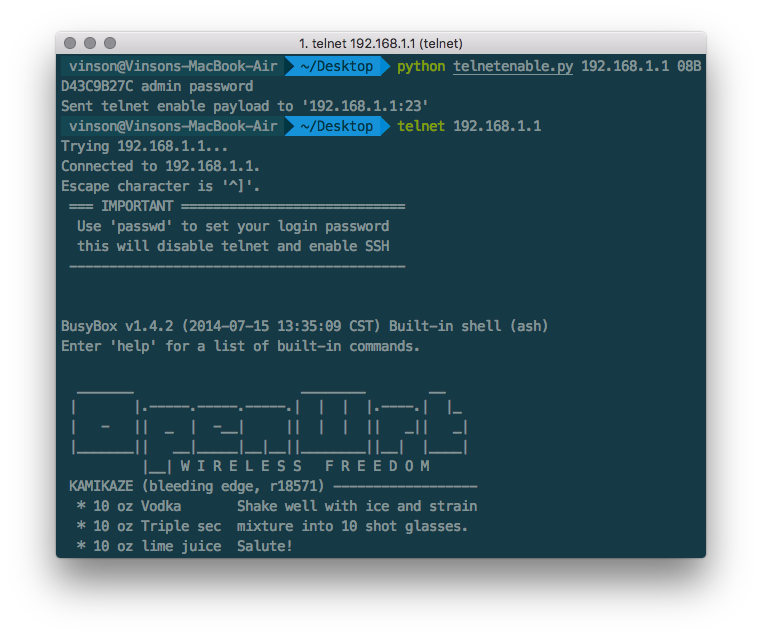
发送成功后会返回 『Sent telnet enable payload to ip』
搭建TFTP服务器
我们登录telnet后,需要在telnet(路由)获取计算机上的下载好的Uboot和固件。于是就需要搭建供telnet访问的TFTP服务器,具体方法见谷歌。然后将Uboot和固件放在TFTP根目录。
获取文件&&刷机
1.刷入Unlock Uboot
cd /tmp
tftp -g -r uboot_env_bootcmd_nocrc.backup 192.168.1.10 69
mtd -f write uboot_env_bootcmd_nocrc.backup u-boot-env
2.刷入OpenWrt固件
tftp -g -r sysfsupgrade.bin 192.168.1.10 69
mtd -f -r write sysfsupgrade.bin firmware
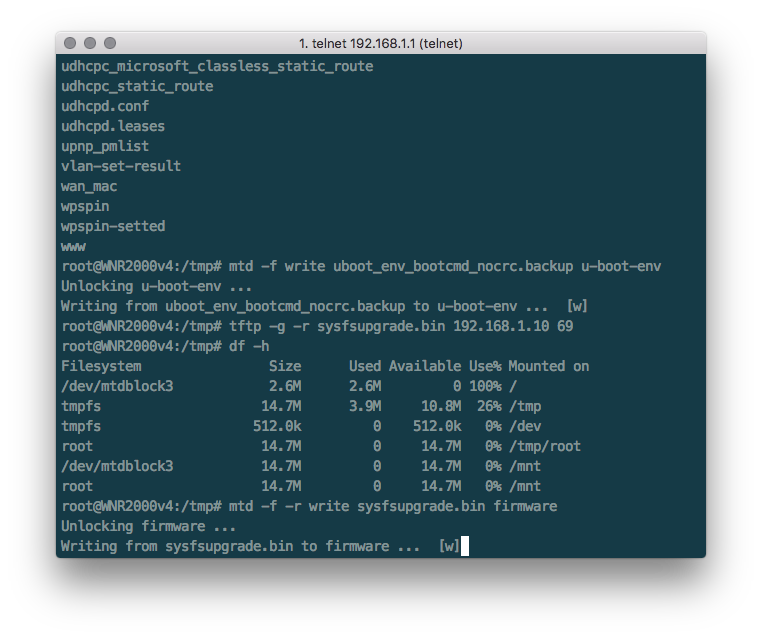
当一切完成后,路由会自动重启
进入OpenWrt
继续使用网线连接,并在浏览器打开’192.168.1.1′
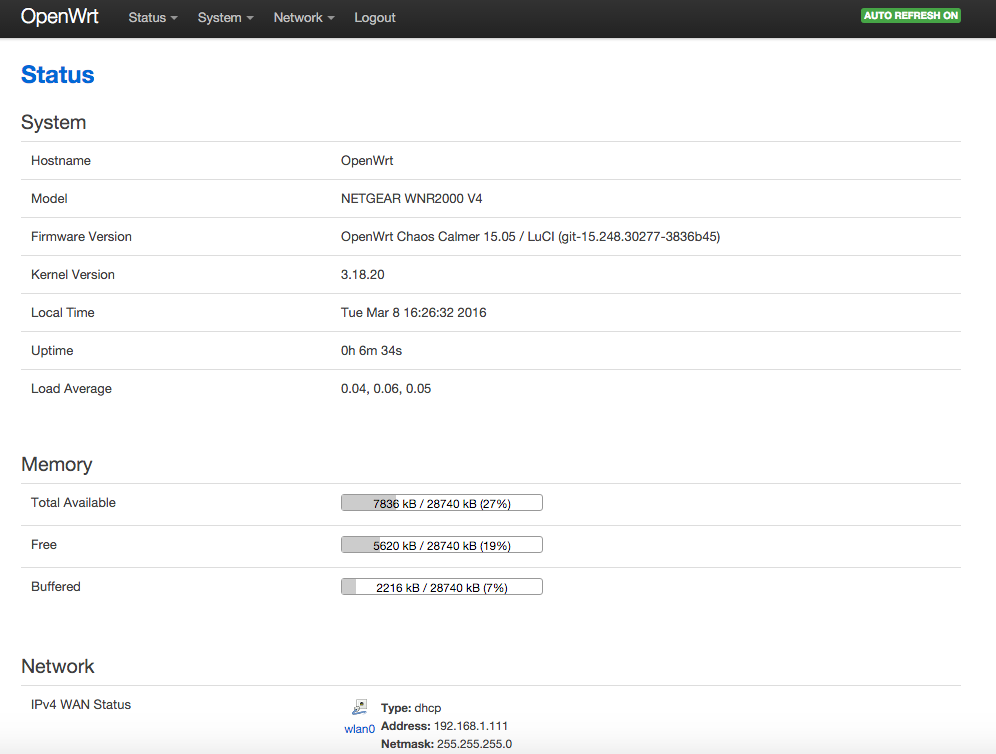
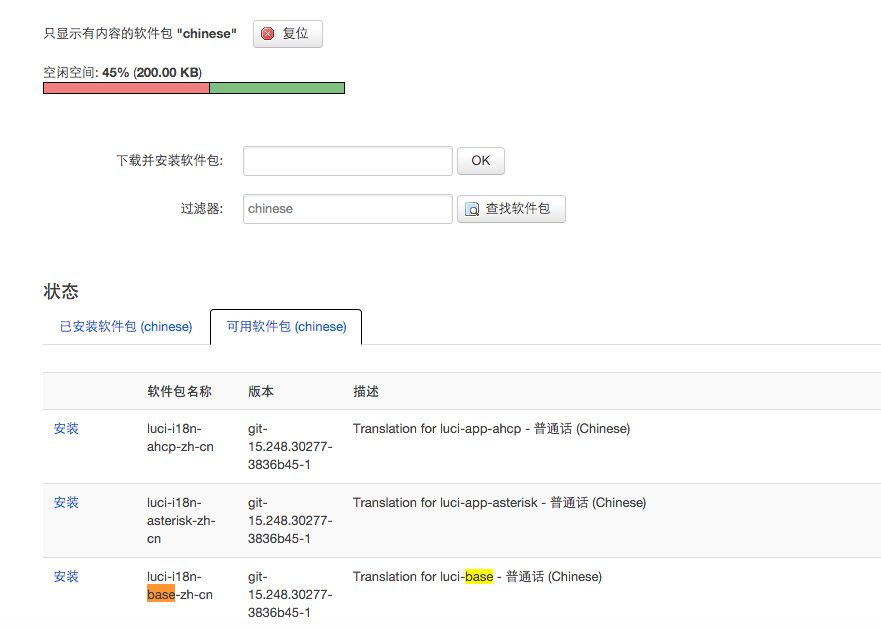
设置使用中文界面,需要在’软件包’-‘过滤器’输入chinese,然后安装luci-i18n-base-zh-cn
发表回复